The Ultimate Guide to Ransomware
2025 edition
Overview
Ransomware is malware designed to virtually mimic the age-old crime of capturing items of value and demanding money for their safe return. Ransomware typically arrives via email or a backdoor, locks up valuable computer files, and is followed by a demand for compensation, often in Bitcoin or another cryptocurrency. The hacker promises a decryption tool on payment of the ransom – but there is never any guarantee of delivery or efficacy of the decryption tool.
Analyst reports

AV-TEST on Malware
Kaspersky wins nine AV-TEST awards for cybersecurity ex...
This month

Gartner on Cybersecurity
Safebreach launches platform for enterprise cyber risk ...
Fri, 7th Feb 2025

Gartner on DevOps
SafeBreach launches new exposure validation platform
Thu, 6th Feb 2025

Gartner on Advanced Persistent Threat Protection
Semperis achieves ARR milestone with USD $100 million m...
Fri, 31st Jan 2025

IDC MarketScape on Malware
Sophos MDR services protect 26,000 organisations global...
Tue, 14th Jan 2025
Featured news

About Shadow IT
Google Threat Intelligence explains China’s evolving cy...
Last week

About Data Protection
Exclusive: ThreatLocker's Danny Jenkins urges firms to ...
This month

About Cloud Services
Exclusive: Why every day should be World Backup Day
This month

About Cryptocurrency
Exclusive: Cyber threats escalate as Australian organis...
Last month

About Firewalls
Exclusive: SonicWall’s Yuvraj Pradhan discusses 2025 se...
Thu, 23rd Jan 2025
Expert columns

By Chris Boyd of Rapid7
2025 Ransomware: Business as Usual, Business is Booming
Last week

By Rakesh Prabhakar of Zoho
How can small and medium businesses safeguard against r...
Last week

By Rashid Mohiuddin of Connected Health, Wavelink
How to protect legacy medical devices from modern cyber...
Last week

By Bryan Marlatt of CyXcel
Cyberattacks: A ticking time bomb for financial stabili...
This month

By William Oh of BlueVoyant
DBS & Bank of China Singapore hit by cyberattack
This month
Interviews

Discussing Shadow IT
Google Threat Intelligence explains China’s evolving cy...
Last week

Discussing Data Protection
Exclusive: ThreatLocker's Danny Jenkins urges firms to ...
This month

Discussing Cloud Services
Exclusive: Why every day should be World Backup Day
This month

Discussing Cryptocurrency
Exclusive: Cyber threats escalate as Australian organis...
Last month

Discussing Firewalls
Exclusive: SonicWall’s Yuvraj Pradhan discusses 2025 se...
Thu, 23rd Jan 2025
More expert columns

By Karthik Raju of Radware
The bot battle: How to defend against scraping attacks
This month

By Oscar Morales of Calian IT & Cyber Solutions
Cloud security in 2025: Why proactive defense is critic...
This month

By Peter Philipp of Neo4j
How graph databases are improving the resilience of sup...
Last month
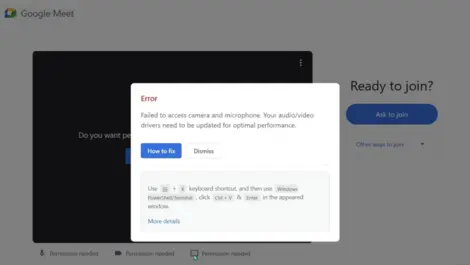
By Dakshitaa Babu of SquareX
Why ClickFix attacks are outpacing enterprise security
Last month

By Gareth Russell of Commvault
Observations on the state of cyber readiness
Last month

By Anthony Spiteri of Veeam
Government Strategies Against Cybercrime: A Deep Dive
Last month
Recent news

About Storage
Hitachi Vantara unveils VSP One with AI ransomware defe...
Last week

About Risk & Compliance
Cyber Threat Insure launches new model for MSPs in Aust
Last week

About Data Protection
Australia's cyber sector grows amid increasing attack r...
Last week

About Malware
Southeast Asian firms face surge in ransomware attacks ...
Last week

About Local government
Australian firms move to passkeys as cyber threats bypa...
Last week
More news

About Firewalls
Cyber security must focus on root causes, not just tool...
Last week

About Digital Transformation
UK firms face rising cyberwarfare threats & GBP £14.2m ...
Last week

About Local government
Australian councils urged to adopt managed security ser...
Last week

About Threat intelligence
Report explores Russian cyber underground's global impa...
This month

About Threat intelligence
AI amplifies cyber threat; non-human identities at risk
This month
Even more news

About Cloud Services
Zscaler report urges shift from VPNs to Zero Trust
This month

About Threat intelligence
Fast Flux DNS tactics escalate cyber defence challenges
This month

About Business Continuity
Commvault & SimSpace launch cyber recovery training
This month

About Hyperscale
Human error tops cloud security threats in Qualys repor...
This month

About Firewalls
Sophos report highlights urgency of active cyber defenc...
This month
Job moves

Move at Cohesity
Cohesity strengthens security with new advisory additio...
Fri, 17th Jan 2025

Move at Fujitsu
OpSys appoints Shanna Daly as first Chief Security Offi...
Mon, 28th Oct 2024

Move at Sophos
Sophos appoints new Chief Revenue Officer & VP of Sales
Thu, 24th Oct 2024

Move at Sophos
Sophos appoints Teresa Anania as new Chief Customer Off...
Tue, 23rd Jul 2024

Move at NetApp
Mark Fioretto named NetApp's new VP for Australia & New...
Tue, 16th Jul 2024
Other guides
You can read other related guides from Cybersecurity, Malware, Breach Prevention, Advanced Persistent Threat Protection, and Artificial Intelligence.
Powered by